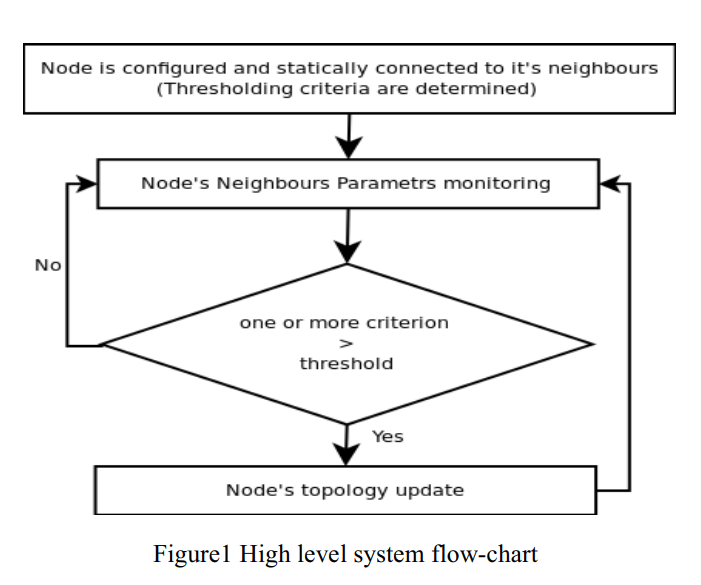
Janitor, certificate and jury (JCJ): Trust scheme for wireless ad-hoc networks
Ad hoc networks are peer mobile nodes that self configure to form a network. In these types of networks there is no routing infrastructure, and usually nodes have limited resources. This imposes a serious problem due to some nodes' selfishness and willingness to preserve their resources. Many approaches have been proposed to deal with this problem and mitigate the selfishness; amongst these approaches are reputation systems. This paper proposes a reputation system scheme that helps isolating misbehaving nodes and decreasing their ability to launch an attack on the network. The idea of this
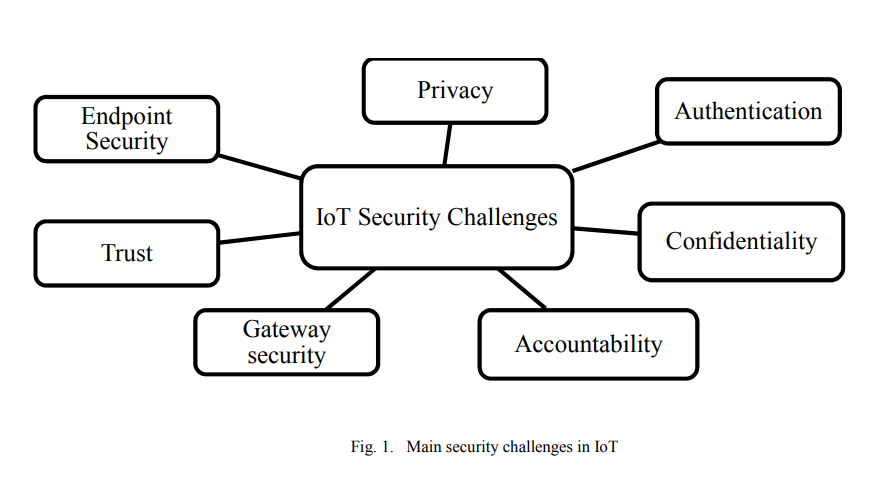
Internet of Things security framework
For the past decade, Internet of Things (IoT) had an important role in our lives. It connects a large number of embedded devices. These devices fulfill very difficult and complicated tasks, which facilitate our work. Till now the security of IoT faces many challenges such as privacy, authentication, confidentiality, trust, middleware security, mobile security and policy enforcement. In order to provide a secure environment for IoT, this paper proposes a framework for IoT devices. © 2017 IEEE.
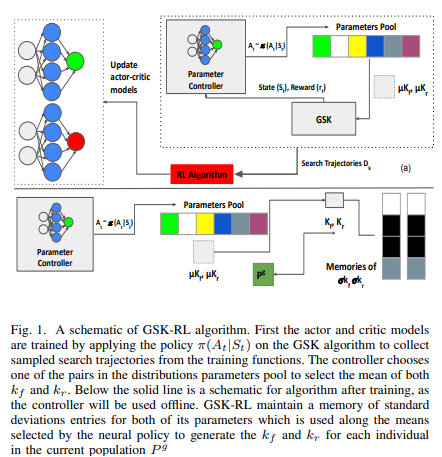
GSK-RL: Adaptive Gaining-sharing Knowledge algorithm using Reinforcement Learning
Meta-heuristics and nature inspired algorithms have been prominent solvers for highly complex, nonlinear and hard optimization problems. The Gaining-Sharing Knowledge algorithm (GSK) is a recently proposed nature-inspired algorithm, inspired by human and their tendency towards growth and gaining and sharing knowledge with others. The GSK algorithm have been applied to different optimization problems and proved robustness compared to other nature-inspired algorithms. The GSK algorithm has two main control parameters kfand kr which controls how much individuals gain and share knowledge with

A survey on smart cities’ IoT
The rise of the Internet of Things (IoT) has led to a numerous and diverse amount of products and real life implementations for smart cities in the last few years. With the many opportunities and challenges, the academic and industrial field has come up with many hardware and middleware platforms. We categorise these different IoT applications and solutions into different domains and present an application for each. This survey aims at defining the state-of-the-art major and common technologies, frameworks, and applications used to open doors to drive future research and to spark new ideas for
An approach for extracting and disambiguating arabic persons' names using clustered dictionaries and scored patterns
Building a system to extract Arabic named entities is a complex task due to the ambiguity and structure of Arabic text. Previous approaches that have tackled the problem of Arabic named entity recognition relied heavily on Arabic parsers and taggers combined with a huge set of gazetteers and sometimes large training sets to solve the ambiguity problem. But while these approaches are applicable to modern standard Arabic (MSA) text, they cannot handle colloquial Arabic. With the rapid increase in online social media usage by Arabic speakers, it is important to build an Arabic named entity
Traffisense: A smart integrated visual sensing system for traffic monitoring
Intelligent camera systems provide an effective solution for road traffic monitoring with traffic stream characteristics, such as volumes and densities, continuously computed and relayed to control stations. However, developing a functional vision-based traffic monitoring system is a complex task that entails the creation of appropriate visual sensing platforms with on-board visual analytics algorithms, integration of versatile technologies for data provision and stream management, and development of data visualization techniques suitable for end-users. This paper describes TraffiSense, a
Towards IT-Legal Framework for Cloud Computing
As the common understanding of Cloud Computing is continuously evolving, the terminology and concepts used to define it often need clarifying. Therefore, Cloud customers and Cloud Providers are used to dispute about Service Level Agreements, Service Level Objectives and Quality of Service. Simultaneously, SLAs/SLOs/QoS represent other related technical problems such as Security, Privacy, Compliancy and others. Technical problems are usually defined within technical context, where both parties ignore analyzing problem's legally related causes. In fact, these problems are stemming from the
Transform domain two dimensional and diagonal modular principal component analysis for facial recognition employing different windowing techniques
Spatial domain facial recognition Modular IMage Principal Component Analysis (MIMPCA) has an improved recognition rate compared to the conventional PCA. In the MPCA, face images are divided into smaller sub-images and the PCA approach is applied to each of these sub-images. In this work, the Transform Domain implementation of MPCA is presented. The facial image has two representations. The Two Dimensional MPCA (TD-2D-MPCA) and the Diagonal matrix MPCA (TD-Dia-MPCA). The sub-images are processed using both non-overlapping and overlapping windows. All the test results, for noise free and noisy
Honey Badger Algorithm: New metaheuristic algorithm for solving optimization problems
Recently, the numerical optimization field has attracted the research community to propose and develop various metaheuristic optimization algorithms. This paper presents a new metaheuristic optimization algorithm called Honey Badger Algorithm (HBA). The proposed algorithm is inspired from the intelligent foraging behavior of honey badger, to mathematically develop an efficient search strategy for solving optimization problems. The dynamic search behavior of honey badger with digging and honey finding approaches are formulated into exploration and exploitation phases in HBA. Moreover, with
Towards Efficient Online Topic Detection through Automated Bursty Feature Detection from Arabic Twitter Streams
Detecting trending topics or events from Twitter is an active research area. The first step in detecting such topics focuses on efficiently capturing textual features that exhibit an unusual high rate of appearance during a specific timeframe. Previous work in this area has resulted in coining the term "detecting bursty features" to refer to this step. In this paper, TFIDF, entropy, and stream chunking are adapted to investigate a new technique for detecting bursty features from an Arabic Twitter stream. Experimental results comparing bursty features extracted from Twitter streams, to Twitter
Pagination
- Previous page ‹‹
- Page 5
- Next page ››
