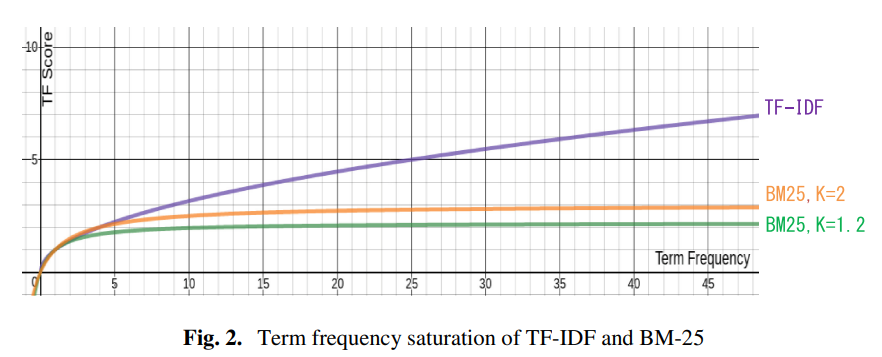
Behaviorally-Based Textual Similarity Engine for Matching Job-Seekers with Jobs
Understanding both of job-seekers and employers behavior in addition to analyzing the text of job-seekers and job profiles are two important missions for the e-recruitment industry. They are important tasks for matching job-seekers with jobs to find the top relevant suggestions for each job-seeker. Recommender systems, information retrieval and text mining are originally targeted to assist users and provide them with useful information, which makes human-computer interaction plays a fundamental role in the users’ acceptance of the produced suggestions. We introduce our intelligent framework to
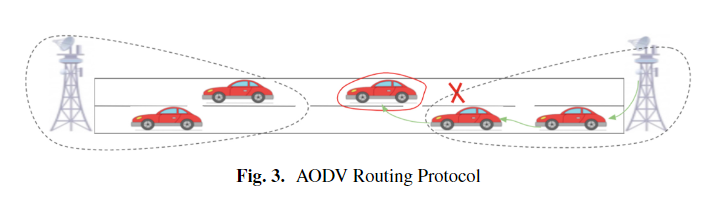
A Comprehensive Survey on Vehicular Ad Hoc Networks (VANET)
Vehicular Ad Hoc Networks is an evolving research field that has the potential to address safety on roads. This tends to attract car manufacturers and suppliers to develop in evolving the industry vision. VANET demonstrates a different kind of communications targeting the main objective, which is safety besides entertainment services. This is achieved using the Internet through the infrastructure units located aside on the roads. In this paper, the main concern is safety-oriented communication, V2V, and V2I, which are often used together to achieve the required safety objectives. We focus on
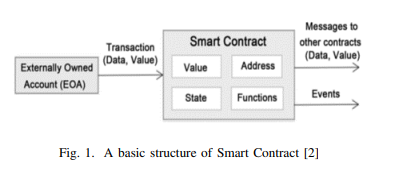
Efficient Quering Blockchain Applications
Industrial blockchain applications have recently risen to the top of the scientific and industrial communities' priority lists. This is due to their practical capabilities in resolving many issues in various industrial domains. Visibility and traceability to a large volume of trusted data benefit members of a consortium of industrial companies and associated organizations. Data scientists who query data and use statistics and Machine Learning to solve a wide range of interesting problems benefit as well. This paper introduces a blockchain application Query Engine based on upgradable Smart
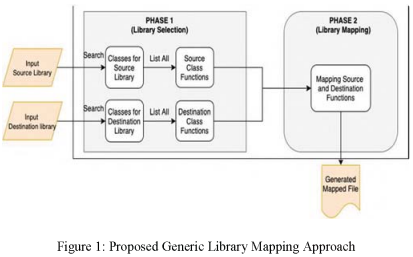
Generic Library Mapping Approach for Trans-Compilation
Cross-platform mobile development is a widely used framework due to its nature of building an app using one development life cycle and deploying it to multiple platforms like Android and iOS. Many cross-platform solutions were recently developed to convert from one platform to another using Trans-compilation approach as Trans-Compiler Android to IOS Conversion (TCAIOSC) and Trans-Compiler Based Mobile Applications code converter. The limitations of these solutions is that they are unable to convert a library function that was not previously included by the developer. In this paper, a generic
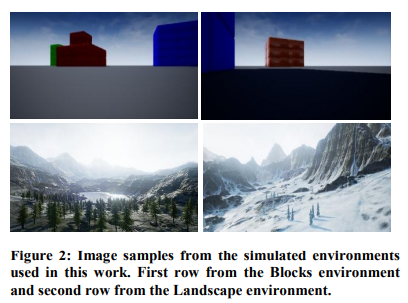
Deep convolutional neural network based autonomous drone navigation
This paper presents a novel approach for aerial drone autonomous navigation along predetermined paths using only visual input form an onboard camera and without reliance on a Global Positioning System (GPS). It is based on using a deep Convolutional Neural Network (CNN) combined with a regressor to output the drone steering commands. Furthermore, multiple auxiliary navigation paths that form a â€n˜avigation envelope' are used for data augmentation to make the system adaptable to real-life deployment scenarios. The approach is suitable for automating drone navigation in applications that
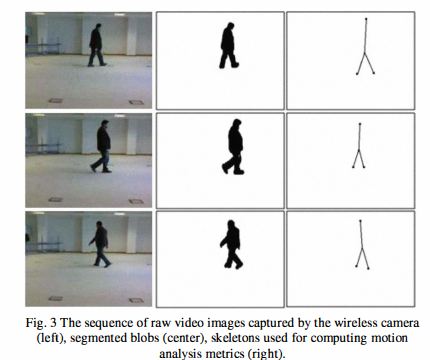
Ambient and wearable sensing for gait classification in pervasive healthcare environments
Pervasive healthcare environments provide an effective solution for monitoring the wellbeing of the elderly where the general trend of an increasingly ageing population has placed significant burdens on current healthcare systems. An important pervasive healthcare system functionality is patient motion analysis where gait information can be used to detect walking behavior abnormalities that may indicate the onset of adverse health problems, for quantifying post-operative recovery, and to observe the progression of neurodegenerative diseases. The development of accurate motion analysis models
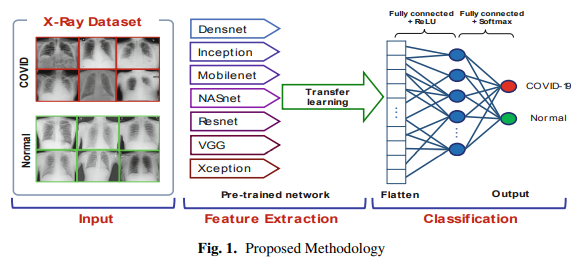
Detection of COVID-19 from Chest X-Ray Images Using Deep Neural Network with Fine-Tuning Approach
The coronavirus (COVID-2019) quickly spread throughout the world and came to be a pandemic. To avoid further spreading this epidemic and treat affected patients rapidly, it is important to recognize the positive cases as early as possible. In this paper, deep learning techniques are employed to detect COVID-19 from chest X-ray images quickly. The images of the two classes, COVID and No-findings are collected from three public datasets. The proposed approach consists of two phases; transfer learning and fine-tuning. Transfer learning is carried out by seven deep learning models: DenseNet
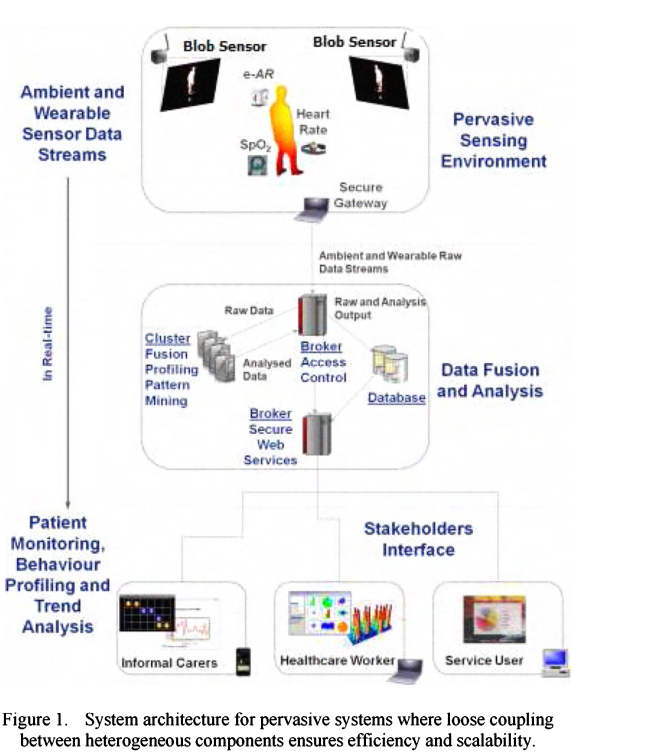
An integrated multi-sensing framework for pervasive healthcare monitoring
Pervasive healthcare provides an effective solution for monitoring the wellbeing of elderly, quantifying post-operative patient recovery and monitoring the progression of neurodegenerative diseases such as Parkinson's. However, developing functional pervasive systems is a complex task that entails the creation of appropriate sensing platforms, integration of versatile technologies for data stream management and development of elaborate data analysis techniques. This paper describes a complete and an integrated multi-sensing framework, with which the sensing platforms, data fusion and analysis
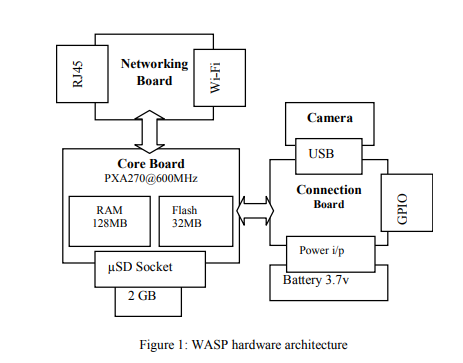
WASP: Wireless autonomous sensor prototype for Visual Sensor Networks
Visual Sensor Networks (VSNs) enable enhanced three-dimensional sensing of spaces and objects, and facilitate collaborative reasoning to open up a new realm of vision-based distributed smart applications including security/surveillance, healthcare delivery, traffic monitoring, just to name a few. However, such applications require sensor nodes that can efficiently process large volumes of visual information in-situ and exhibit intelligent behavior to support autonomous operation, scalability, and energy efficiency. This paper presents WASP, a vision sensor node prototype with high
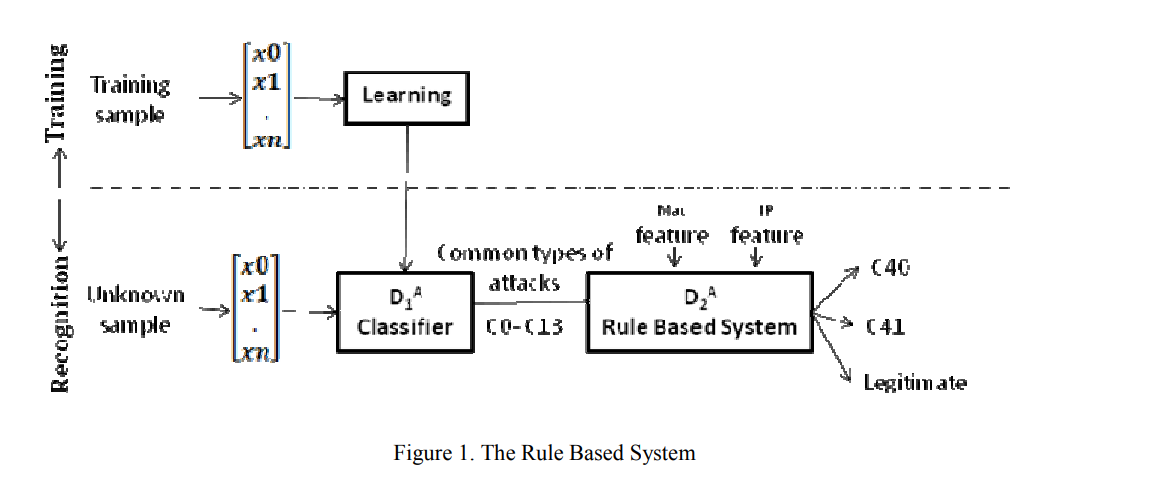
Misfeasor classification and detection models using machine learning techniques
Misfeasors (or insiders) are considered among the most difficult intruders to detect due to their knowledge and authorization within the organization. Machine learning techniques have been widely used for intrusion detection but only little work has addressed the use of machine learning for detecting and classifying different types of insiders. The aim of this study is to exploit different recognition models for misfeasors detection by adding the Mac address as a feature in classification. Three different recognition models (a Rule Based Model, a Hierarchical Classification Model and a
Pagination
- Previous page ‹‹
- Page 13
- Next page ››
