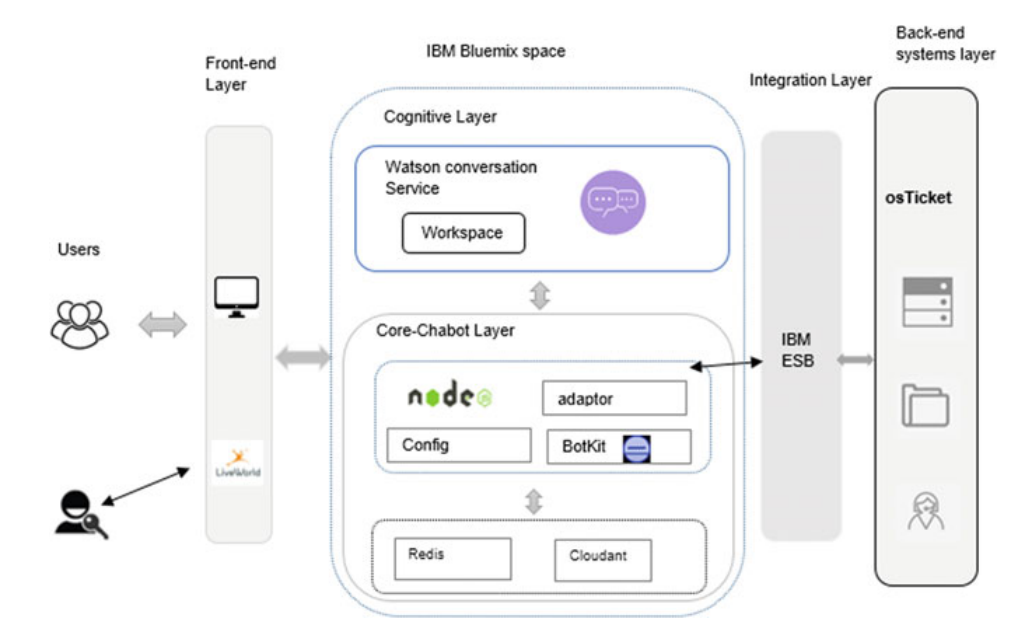
A study about using a cognitive agent in replacing level 1 and 2 service desk activities
The radical change in technology and high customer expectations and demand are pushing the service desk to provide a competent service for the customers. And this service should be faster, more flexible and gives a more accurate response and high user experience. Replacing the human call agent’s activities with a cognitive agent could improve the user experience by providing a faster response to customer’s requests, removing the human errors and giving 24/7 support with less operational cost. The cognitive agent has the potential to scale personalized and tailored interactions. And this will
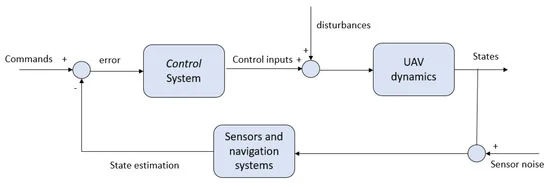
Tracking ground targets from a UAV using new P-N constraints
This paper presents improved automatic moving target detection and tracking framework that is suitable for UAV imagery. The framework is comprised of motion compensation phase to detect moving targets from a moving camera, target state estimation with Kalman filter, and overlap-rate-based data association. Finally, P-N learning is used to maintain target appearance by utilizing novel structural constraints to select positive and negative samples, where data association decisions are used as positive (P) constraints. After learning target appearance, a cascaded classifier is employed to detect
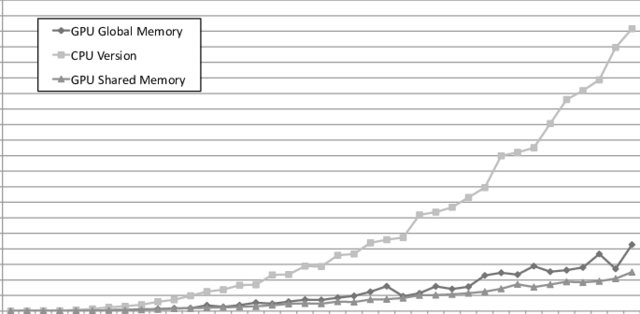
A GPU-enabled solver for time-constrained linear sum assignment problems
This paper deals with solving large instances of the Linear Sum Assignment Problems (LSAPs) under realtime constraints, using Graphical Processing Units (GPUs). The motivating scenario is an industrial application for P2P live streaming that is moderated by a central tracker that is periodically solving LSAP instances to optimize the connectivity of thousands of peers. However, our findings are generic enough to be applied in other contexts. Our main contribution is a parallel version of a heuristic algorithm called Deep Greedy Switching (DGS) on GPUs using the CUDA programming language. DGS
Remote Diagnosis, Maintenance and Prognosis for Advanced Driver Assistance Systems Using Machine Learning Algorithms
New challenges and complexities are continuously increasing in advanced driver assistance systems (ADAS) development (e.g. active safety, driver assistant and autonomous vehicle systems). Therefore, the health management of ADAS’ components needs special improvements. Since software contribution in ADAS’ development is increasing significantly, remote diagnosis and maintenance for ADAS become more important. Furthermore, it is highly recommended to predict the remaining useful life (RUL) for the prognosis of ADAS’ safety critical components; e.g. (Ultrasonic, Cameras, Radar, LIDAR). This paper
Motion and depth augmented semantic segmentation for autonomous navigation
Motion and depth provide critical information in autonomous driving and they are commonly used for generic object detection. In this paper, we leverage them for improving semantic segmentation. Depth cues can be useful for detecting road as it lies below the horizon line. There is also a strong structural similarity for different instances of different objects including buildings and trees. Motion cues are useful as the scene is highly dynamic with moving objects including vehicles and pedestrians. This work utilizes geometric information modelled by depth maps and motion cues represented by
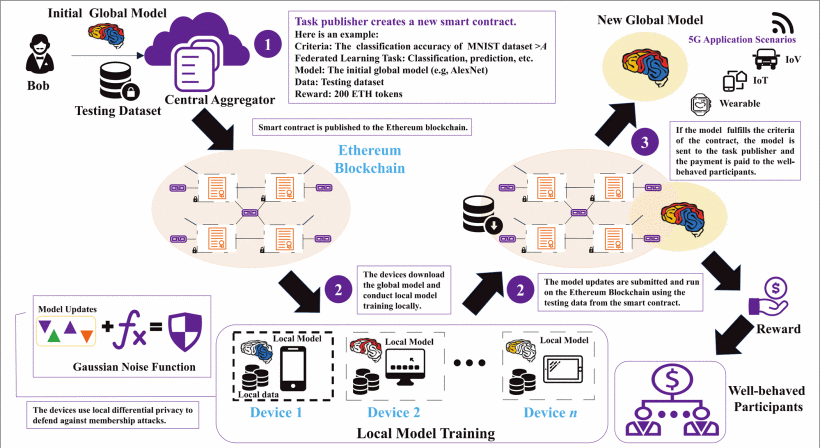
A Secure Federated Learning Framework for 5G Networks
Federated learning (FL) has recently been proposed as an emerging paradigm to build machine learning models using distributed training datasets that are locally stored and maintained on different devices in 5G networks while providing privacy preservation for participants. In FL, the central aggregator accumulates local updates uploaded by participants to update a global model. However, there are two critical security threats: poisoning and membership inference attacks. These attacks may be carried out by malicious or unreliable participants, resulting in the construction failure of global
A detailed survey and future directions of unmanned aerial vehicles (Uavs) with potential applications
Recently, unmanned aerial vehicles (UAVs), also known as drones, have gained widespread interest in civilian and military applications, which has led to the development of novel UAVs that can perform various operations. UAVs are aircraft that can fly without the need of a human pilot onboard, meaning they can fly either autonomously or be remotely piloted. They can be equipped with multiple sensors, including cameras, inertial measurement units (IMUs), LiDAR, and GPS, to collect and transmit data in real time. Due to the demand for UAVs in various applications such as precision agriculture
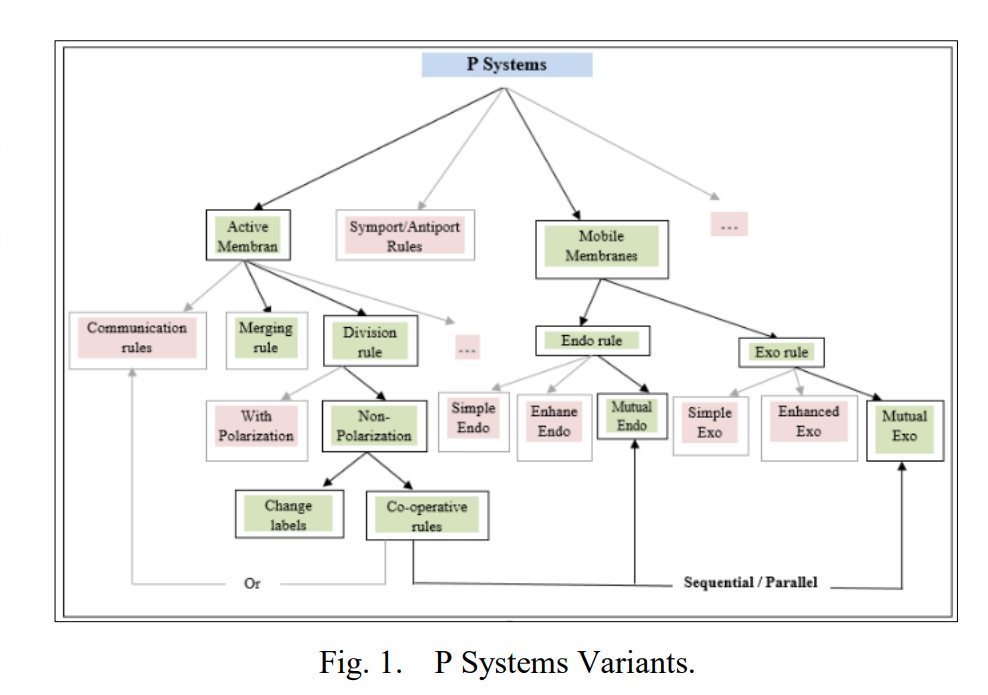
P Systems Implementation: A Model of Computing for Biological Mitochondrial Rules using Object Oriented Programming
Membrane computing is a computational framework that depends on the behavior and structure of living cells. P systems are arising from the biological processes which occur in the living cells’ organelles in a non-deterministic and maximally parallel manner. This paper aims to build a powerful computational model that combines the rules of active and mobile membranes, called Mutual Dynamic Membranes (MDM). The proposed model will describe the biological mechanisms of the metabolic regulation of mitochondrial dynamics made by mitochondrial membranes. The behaviors of the proposed model regulate
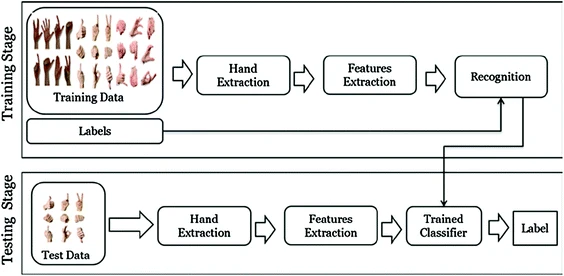
Gesture recognition for improved user experience in augmented biology lab
The Learning process in education systems is one of the most important issues that affect all societies. Advances in technology have influenced how people communicate and learn. Gaming Techniques (GT) and Augmented Reality (AR) technologies provide new opportunities for a learning process. They transform the student’s role from passive to active in the learning process. It can provide a realistic, authentic, engaging and interesting learning environment. Hand Gesture Recognition (HGR) is a major driver in the field of Augmented Reality (AR). In this paper, we propose an initiative Augmented
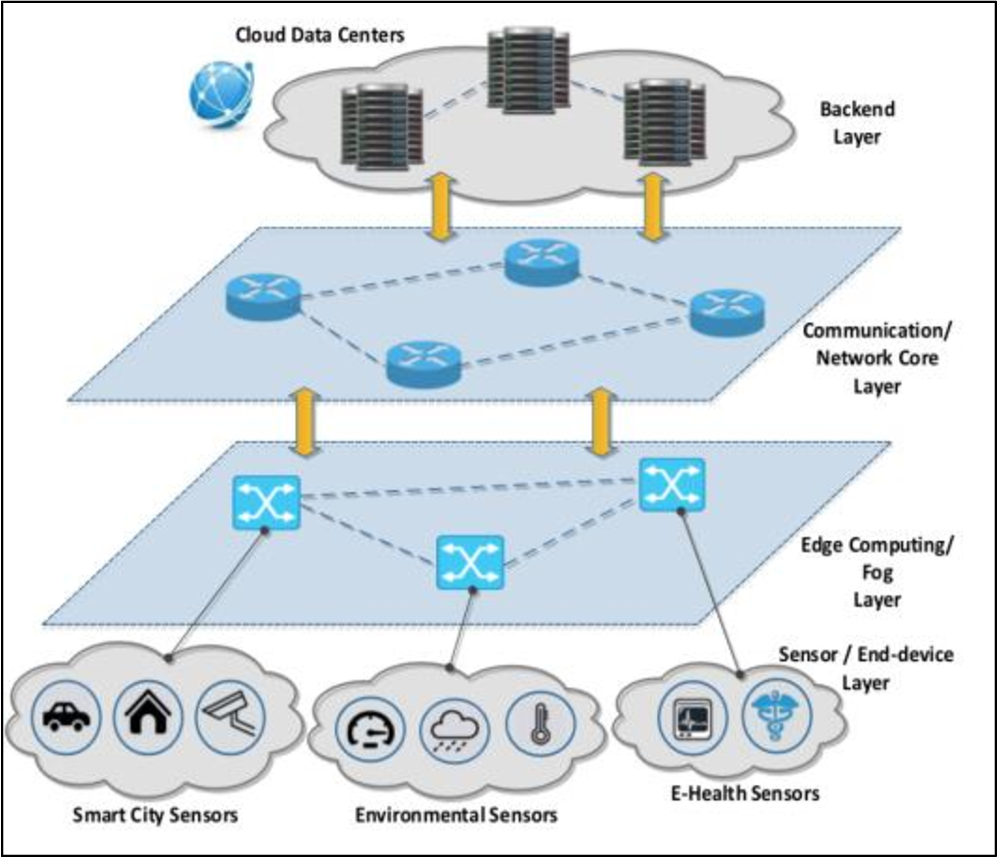
IoT Modes of Operations with Different Security Key Management Techniques: A Survey
The internet of things (IoT) has provided a promising opportunity to build powerful systems and applications. Security is the main concern in IoT applications due to the privacy of exchanged data using limited resources of IoT devices (sensors/actuators). In this paper, we present a classification of IoT modes of operation based on the distribution of IoT devices, connectivity to the internet, and the typical field of application. It has been found that the majority of IoT services can be classified into one of four IoT modes: Gateway, device to device, collaborative, and centralized. The
Pagination
- Previous page ‹‹
- Page 12
- Next page ››
