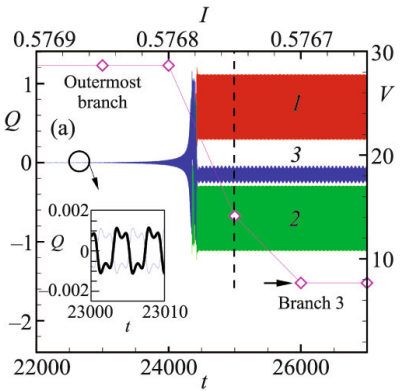
Breathing charge density waves in intrinsic Josephson junctions
We demonstrate the creation of a charge density wave (CDW) along a stack of coupled Josephson junctions (JJs) in layered superconductors. Electric charge in each superconducting layer oscillates around some average value, forming a breathing CDW. We show the transformation of a longitudinal plasma wave to CDW in the state corresponding to the outermost branch. Transition between different types of CDW's related to the inner branches of IV characteristic is demonstrated. The effect of the external electromagnetic radiation on the states corresponding to the inner branches differs crucially from
Reliability and Security Analysis of an Entanglement-Based QKD Protocol in a Dynamic Ground-to-UAV FSO Communications System
Quantum cryptography is a promising technology that achieves unconditional security, which is essential to a wide range of sensitive applications. In contrast to optical fiber, the free-space optical (FSO) link is efficiently used as a quantum channel without affecting the polarization of transmitted photons. However, the FSO link has several impairments, such as atmospheric turbulence and pointing errors, which affect the performance of the quantum channel. This paper proposes a quantum key distribution (QKD) scheme that uses a time-bin entanglement protocol over the FSO channel that suffers
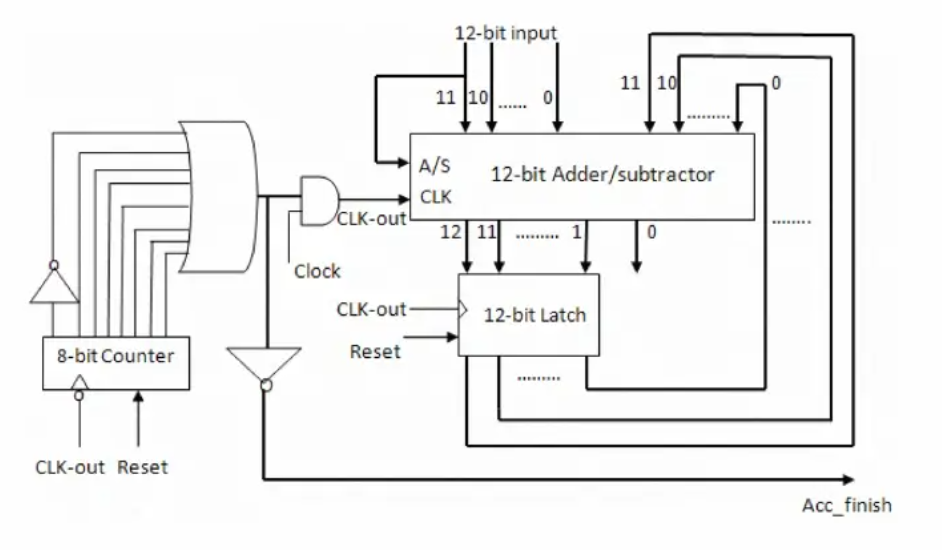
A simplification in integral frequency offset estimation based on joint detection algorithm for WiMAX 802.16e
Initial downlink synchronization for orthogonal frequency division multiple access ( OFDMA ) network access involves timing and frequency synchronization. The frequency offset is produced by oscillator drifts and time-varying Doppler shifts. In mobile WiMAX 802.16e carrier frequency offset (CFO) can be divided into: integral carrier frequency offset (ICFO) and fractional carrier frequency offset (FCFO). There are mainly three methods for CFO estimation: data-aided method, blind and semi-blind. This paper is based on the semi-blind method presented in "Joint detection of integral carrier
Tunnel-Based EAP Effective Security Attacks WPA2 Enterprise Evaluation and Proposed Amendments
Tunnel-Based Extensible Authentication Protocol has become fundamental for wireless Network access Control. It provides authentication, privacy and authorization for enterprise network access protected by WPA/WPA2 security framework. WPA2 is considered the latest and most secure standard for wireless communication especially for Wi-Fi networks. However, WPA/WPA2-PSK have been lately threatened by advanced versions of wireless attacks. In this paper, we study WPA/WPA2-Enterprise authentication with Tunnel-Based EAP common methods focusing on their strength and weak points and the impact of
Anonymous routing protocols in MANETs, a security comparative analysis
A Mobile Ad Hoc Network (MANET) is considered a type of network which is wireless and has no fixed infrastructure composed of a set if nodes in self organized fashion which are randomly, frequently and unpredictably mobile. MANETs can be applied in both military and civil environments ones because of its numerous applications. This is due to their special characteristics and self-configuration capability. This is due to its dynamic nature, lack of fixed infrastructure, and the no need of being centrally managed; a special type of routing protocols such as Anonymous routing protocols are needed

Parallel and independent true random bitstreams from optical emission spectra of atmospheric microplasma arc discharge
In this study, we propose the possibility of generating several parallel and independent random bitstreams from the time-varying optical emission spectra of an atmospheric pressure air microplasma system. This is achieved by splitting the plasma arc emission into discrete wavelengths using an optical spectrometer and then monitoring the fluctuating intensities of each wavelength as an independent time series. As a proof of concept, we considered eight wavelengths centered at 377.8, 389.1, 425.8, 591.4, 630.5, 673.0, 714.2, and 776.4 nm corresponding to atomic emissions lines from species
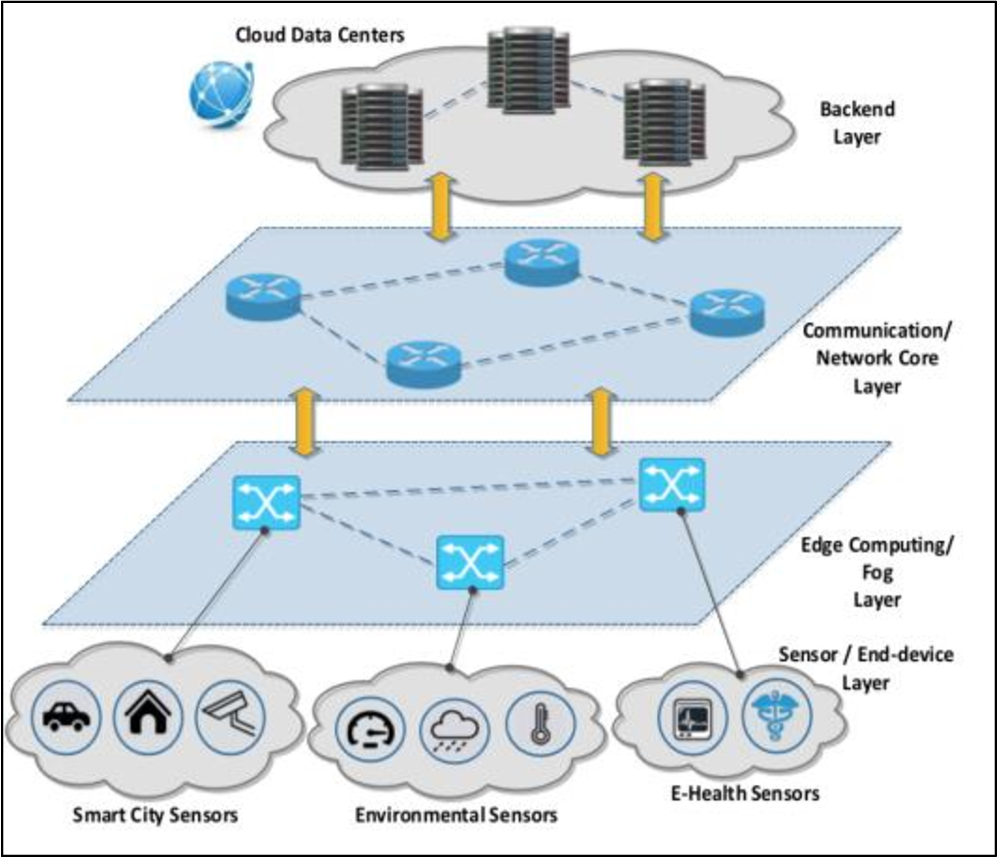
IoT Modes of Operations with Different Security Key Management Techniques: A Survey
The internet of things (IoT) has provided a promising opportunity to build powerful systems and applications. Security is the main concern in IoT applications due to the privacy of exchanged data using limited resources of IoT devices (sensors/actuators). In this paper, we present a classification of IoT modes of operation based on the distribution of IoT devices, connectivity to the internet, and the typical field of application. It has been found that the majority of IoT services can be classified into one of four IoT modes: Gateway, device to device, collaborative, and centralized. The
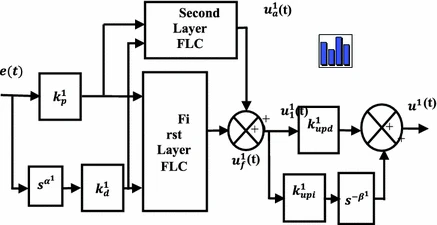
Control of a two link planar electrically-driven rigid robotic manipulator using fractional order SOFC
An intelligent adaptive fuzzy logic control technique, Fractional Order Self Organizing Fuzzy Controller (FOSOFC) is presented and applied to control a two link planar electrically-driven rigid robotic (EDRR) manipulator system. As EDRR is a multi-input multi-output complex nonlinear system, an intelligent adaptive controller, FOSOFC is considered to control it perfectly. To show the efficacy of the FOSOFC controller, the obtained performance is compared with fractional order fuzzy proportional integral and derivative (FOFPID) controller for study in servo as well as the regulatory problems
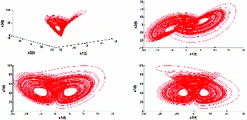
Control of new type of fractional chaos synchronization
Based on stability theory of linear fractional order systems and stability theory of linear integer order systems, the problem of coexistence of various types of synchronization between different dimensional fractional chaotic systems is investigated in this paper. Numerical and simulation results have clearly shown the effectiveness of the novel approach developed herein. © 2018, Springer International Publishing AG.
Real-Time Dorsal Hand Recognition Based on Smartphone
The integration of biometric recognition with smartphones is necessary to increase security, especially in financial transactions such as online payments. Vein recognition of the dorsal hand is superior to other methods such as palm, finger, and wrist, as it has a wide area to be captured and does not have any wrinkles. Most current systems that depend on dorsal hand vein recognition do not work in real-time and have poor results. In this paper, a dorsal hand recognition system working in real-time is proposed to achieve good results with a high frame rate. A contactless device consists of a
Pagination
- Previous page ‹‹
- Page 3
- Next page ››
