In-silico development and assessment of a Kalman filter motor decoder for prosthetic hand control
Up to 50% of amputees abandon their prostheses, partly due to rapid degradation of the control systems, which require frequent recalibration. The goal of this study was to develop a Kalman filter-based approach to decoding motoneuron activity to identify movement kinematics and thereby provide stable, long-term, accurate, real-time decoding. The Kalman filter-based decoder was examined via biologically varied datasets generated from a high-fidelity computational model of the spinal motoneuron pool. The estimated movement kinematics controlled a simulated MuJoCo prosthetic hand. This clear-box
Improved Semantic Segmentation of Low-Resolution 3D Point Clouds Using Supervised Domain Adaptation
One of the key challenges in applying deep learning to solve real-life problems is the lack of large annotated datasets. Furthermore, for a deep learning model to perform well on the test set, all samples in the training and test sets should be independent and identically distributed (i.i.d.), which means that test samples should be similar to the samples that were used to train the model. In many cases, however, the underlying training and test set distributions are different. In such cases, it is common to adapt the test samples by transforming them to their equivalent counterparts in the
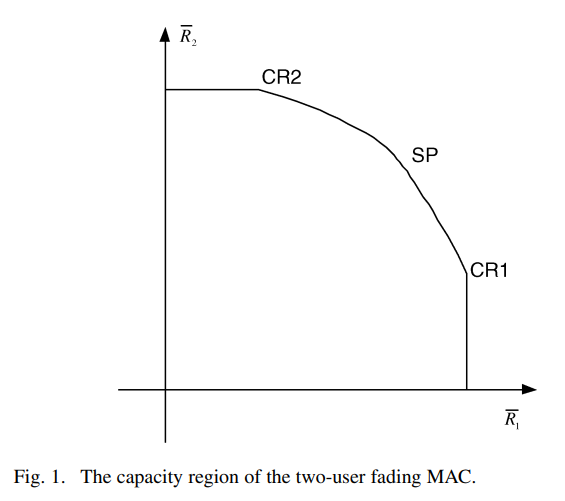
The water-filling game in fading multiple-access channels
A game-theoretic framework is developed to design and analyze the resource allocation algorithms in fading multiple-access channels (MACs), where the users are assumed to be selfish, rational, and limited by average power constraints. The maximum sum-rate point on the boundary of the MAC capacity region is shown to be the unique Nash equilibrium of the corresponding water-filling game. This result sheds a new light on the opportunistic communication principle. The base station is then introduced as a player interested in maximizing a weighted sum of the individual rates. A Stackelberg

Towards a federated network architecture
The layered architecture that guided the design of the Internet is deemed inadequate as a reference model for engineering protocols for NGN. Layered protocol suites impose a strict sequential order on protocol execution conflicting with the efficient engineering of end systems, as well as failing to express vertical functional integration, the separation of control and data planes, and the distributed nature of network functions. Furthermore, protocols developed according to the layered architecture are implemented as monolithic blocks with undefined or implicit dependencies lacking

The relay-eavesdropper channel: Cooperation for secrecy
This paper establishes the utility of user cooperation in facilitating secure wireless communications. In particular, the four-terminal relay-eavesdropper channel is introduced and an outer-bound on the optimal rate-equivocation region is derived. Several cooperation strategies are then devised and the corresponding achievable rate-equivocation region are characterized. Of particular interest is the novel noise-forwarding (NF) strategy, where the relay node sends codewords independent of the source message to confuse the eavesdropper. This strategy is used to illustrate the deaf helper
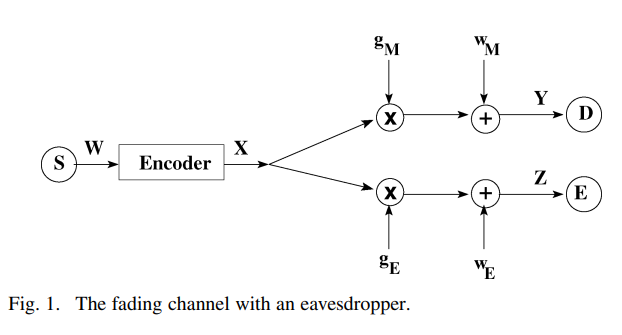
On the secrecy capacity of fading channels
We consider the secure transmission of information over an ergodic fading channel in the presence of an eavesdropper. Our eavesdropper can be viewed as the wireless counterpart of Wyner's wiretapper. The secrecy capacity of such a system is characterized under the assumption of asymptotically long coherence intervals. We first consider the full channel state information (CSI) case, where the transmitter has access to the channel gains of the legitimate receiver and the eavesdropper. The secrecy capacity under this full CSI assumption serves as an upper bound for the secrecy capacity when only
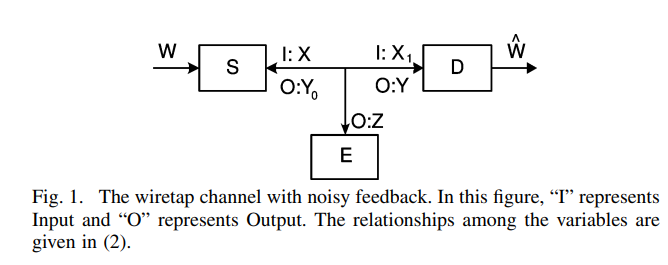
The wiretap channel with feedback: Encryption over the channel
In this work, the critical role of noisy feedback in enhancing the secrecy capacity of the wiretap channel is established. Unlike previous works, where a noiseless public discussion channel is used for feedback, the feed-forward and feedback signals share the same noisy channel in the present model. Quite interestingly, this noisy feedback model is shown to be more advantageous in the current setting. More specifically, the discrete memoryless modulo-additive channel with a full-duplex destination node is considered first, and it is shown that the judicious use of feedback increases the
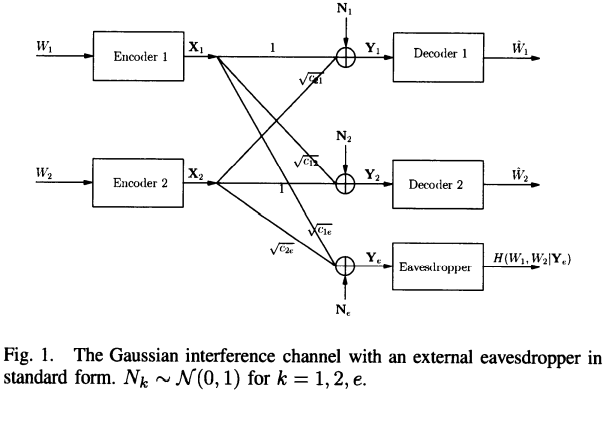
On the secrecy rate region for the interference channel
This paper studies interference channels with security constraints. The existence of an external eavesdropper in a two-user interference channel is assumed, where the network users would like to secure their messages from the external eavesdropper. The cooperative binning and channel prefixing scheme is proposed for this system model which allows users to cooperatively add randomness to the channel in order to degrade the observations of the external eavesdropper. This scheme allows users to add randomness to the channel in two ways: 1) Users cooperate in their design of the binning codebooks

Distributed flooding-based storage algorithms for large-scale wireless sensor networks
In this paper we propose distributed storage algorithms for large-scale wireless sensor networks. Assume a wireless sensor network with n nodes that have limited power, memory, and bandwidth. Each node is capable of both sensing and storing data. Such sensor nodes might disappear from the network due to failures or battery depletion. Hence it is desired to design efficient schemes to collect data from these n nodes. We propose two distributed storage algorithms (DSA's) that utilize network flooding to solve this problem. In the first algorithm, DSA-I, we assume that the total number of sensors
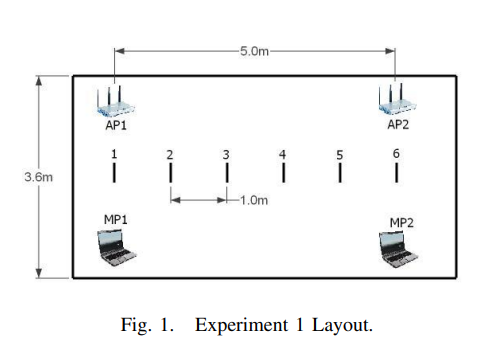
Analysis of a device-free passive tracking system in typical wireless environments
Device-free Passive (DfP) localization is a new concept in location determination where the tracked entity does not carry any device nor participate actively in the localization process. A DfP system operates by processing the received physical signal of a wireless transmitter at one or more monitoring points. The previously introduced DfP system was shown to enable the tracking of a single intruder with high accuracy in a highly controlled WLAN environment. In this paper, we propose and analyze different algorithms for DfP tracking in a typical indoor WLAN environment, rich in multipath. We
Pagination
- Previous page ‹‹
- Page 17
- Next page ››
