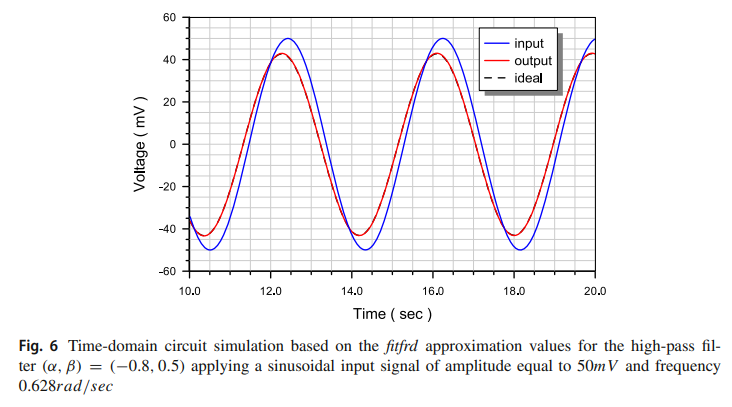
Double Exponent Fractional-Order Filters: Approximation Methods and Realization
The main goal of this work is to exploit different tools in order to approximate a general double exponent fractional-order transfer function. Through the appropriate selection of the two fractional orders of this function, different types of filters can be derived. The investigated approximation tools are either curve fitting based tools or the Padé approximation tool, and the derived approximated transfer functions in all cases have the form of rational integer-order polynomials, which can be easily realized electronically. © 2020, Springer Science+Business Media, LLC, part of Springer
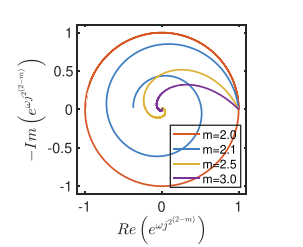
Decoupling the magnitude and phase in a constant phase element
The success of fractional-order fractance (FOF) as a modeling tool in (photo)bio(electro)chemical systems can be readily gauged by the large body of research work that has been conducted over the past few years in terms of materials fabrication, building integer-order emulators of their behavior, as well as applications in filter design, controller design, modeling of energy storage devices and biomaterials. The impedance of FOF has the general form Zα(s)=kαsα where kα and α are real constant and s=jω is the complex Laplace number. In this work, we investigate the possibility of decoupling the
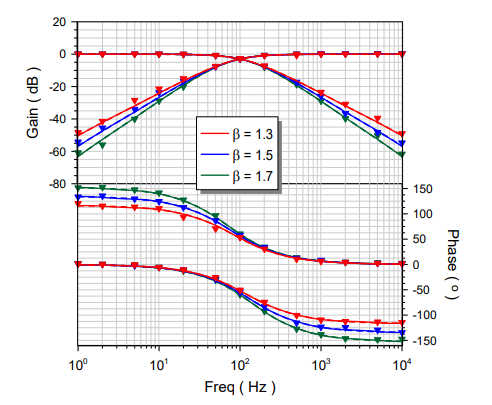
Versatile Field-Programmable Analog Array Realizations of Power-Law Filters
A structure suitable for implementing power-law low-pass and high-pass filter transfer functions is presented in this work. Through the utilization of a field-programmable analog array device, full programmability of the characteristics of the intermediate stages, as is required for realizing the rational integer-order transfer function that approximates the corresponding power-law function, was achieved, making the structure versatile. In addition, a comparison between power-law and fractional-order filters regarding the effect of the non-integer order was performed. The presented design
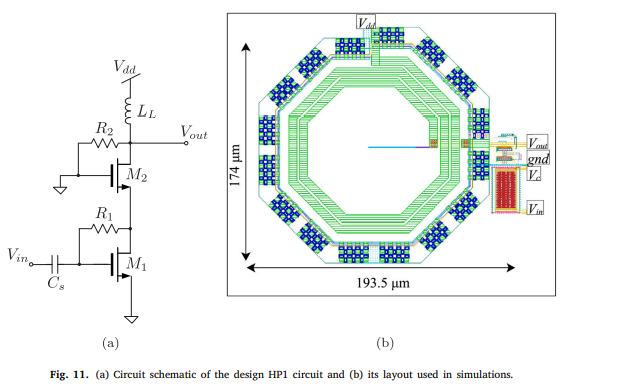
Second-order cascode-based filters
In this paper, we report on the design of a class of analog filters based on the cascode circuit structure surrounded by four impedances. The proposed topology is systematically investigated using two-port network techniques and symbolic math CAD tools. A total of 106 second-order filter circuits can be obtained from this class including 9 low-pass filters, 6 high-pass filters, 73 bandpass filters, 6 band-stop filters, and 12 gain equalizer/all-pass filters. Post-layout simulations in 65-nm CMOS technology of selected members of this family of filters are provided and prove its correct
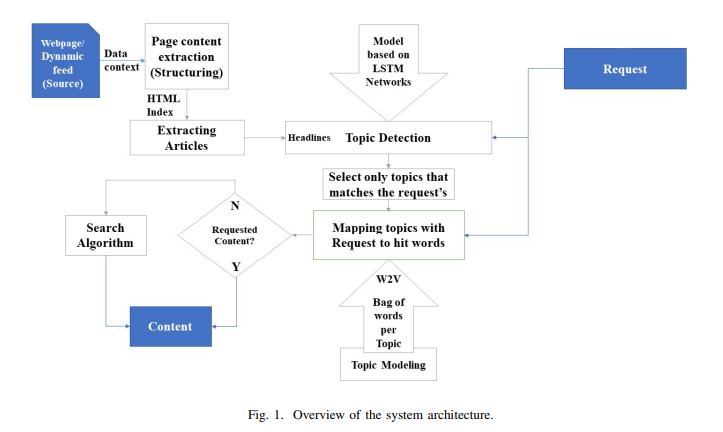
Towards Intelligent Web Context-Based Content On-Demand Extraction Using Deep Learning
Information extraction and reasoning from massive high-dimensional data at dynamic contexts, is very demanding and yet is very hard to obtain in real-time basis. However, such process capability and efficiency might be affected and limited by the available computational resources and the consequent power consumption. Conventional search mechanisms are often incapable of real-time fetching a predefined content from data source, without concerning the increased number of connected devices that contribute to the same source. In this work, we propose and present a concept for an efficient approach
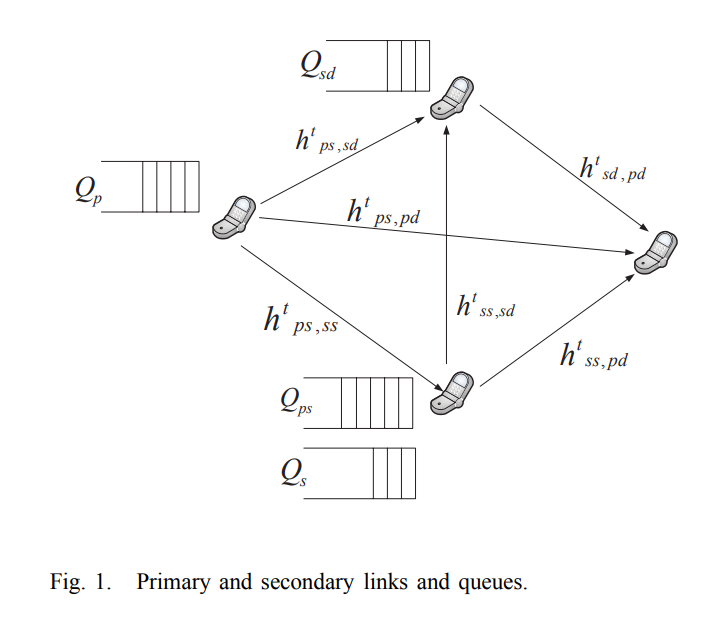
Transmit and receive cooperative cognition: Protocol design and stability analysis
In this paper, we investigate the stability of a cooperative cognitive system. We propose a cooperative secondary transmitter-receiver system (CSTR), where, the secondary transmitter (ST) and the secondary receiver (SR) increase the spectrum availability for the ST packets by relaying the unsuccessfully transmitted packets of the primary transmitter (PT). We assume receiving nodes with multipacket reception capability (MPR). We provide two inner bounds and two outer bounds on the stability region of the considered system. © 2013 ICST - The Institute for Computer Sciences, Social Informatics

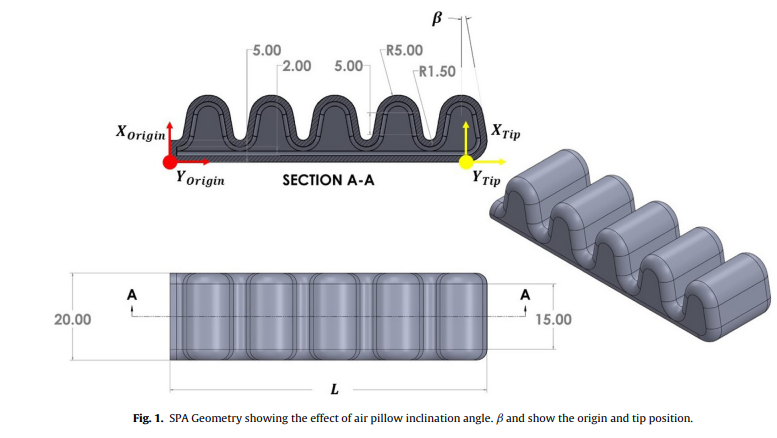
Design and implementation of variable inclined air pillow soft pneumatic actuator suitable for bioimpedance applications
The technological revolution has caused the modernization of human–machine relationship changing our approach in problem solving our society issues and deviated the science of robotic all together. An example for one of the most important pawn in this revolution is soft robotics, the soft robots are robots that are made of deformable materials that provide an alternative approach to rigid robots. The soft pneumatic actuator (SPA) is one of the most widely used and studied form of this type of robotics. In this study, a new geometrical parameter of the SPAs is introduced by studying the effect
Theoretical and experimental investigation study of data driven work envelope modelling for 3D printed soft pneumatic actuators
In the last decade, soft robotics is considered one of the most widely researched fields in robotics, as it has many advantages and more versatile use than rigid robotics. Soft robots are flexible, which enable them to metaphorically complex designs, enabling them to imitate the movement of living things. In this article, the use of regression models with finite element analysis (FEA) data is compared with neural network (NN) models trained on visual feedback data. The effect of the soft pneumatic actuator (SPA) air pillow inclination angle (β) under positive and vacuum pressure on the
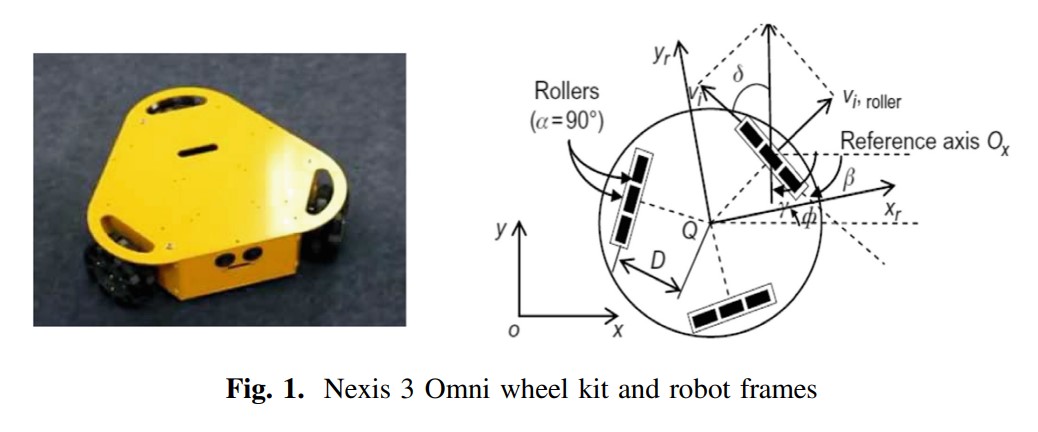
Path Planning Control for 3-Omni Fighting Robot Using PID and Fuzzy Logic Controller
This paper addresses a comparison between some control methods of three Omni wheels firefighting robot due to the variety of maneuverability. To achieve path planning for firefighting robot to reach a specific point with the shortest path, a kinematics model of omni wheel robot is applied with some control algorithms based on PID controller, Fuzzy logic controller and self-tuned PID using fuzzy logic techniques. Hardware prototype has been tested to validate the simulation results. © 2020, Springer Nature Switzerland AG.
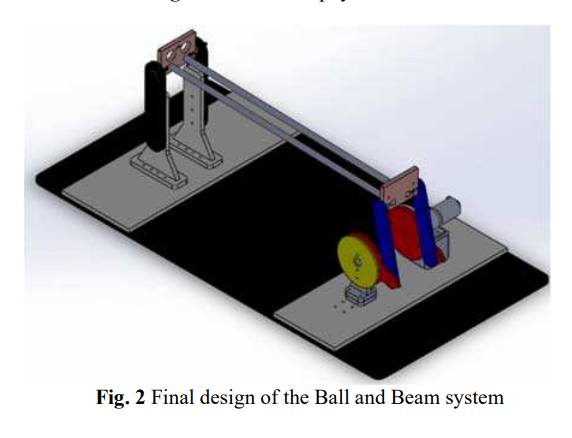
Design and Implementation of a Ball and Beam PID Control System Based on Metaheuristic Techniques
The paper introduces a comparative analysis between three meta-heuristic techniques in the optimization of Proportional-Integral-Derivative (PID) controller for a cascaded control of a ball and beam system. The meta-heuristic techniques presented in this study are Particle Swarm Optimization (PSO), Artificial Bee Colony (ABC) and Bat Algorithm Optimization (BAO). The model uses a DC motor with encoder to move the beam and a camera as a feedback for the ball position on the beam. The control theory of the system depends on two loops; the first (inner) loop is the DC motor for position control
Pagination
- Previous page ‹‹
- Page 14
- Next page ››
