Comparing maintenance strategies for overlays
In this paper, we present an analytical tool for under-standing the performance of structured overlay networks under churn based on the master-equation approach of physics. We motivate and derive an equation for the average number of hops taken by lookups during churn, for the Chord network. We analyse this equation in detail to understand the behaviour with and without churn. We then use this understanding to predict how lookups will scale for varying peer population as well as varying the sizes of the routing tables. We also consider a change in the maintenance algorithm of the overlay, from
Modeling the impacts of information and communication technologies and virtual activities on activity and travel behavior: Case study of Cairo, Egypt
The boom in telecommunications is expected to have many impacts on peoples' activities and travel behavior. Recent advances in information and communication technologies (ICTs) make it possible to conduct activities virtually. Thus the need for physical travel for some types of activities is obviated. Accordingly, the use of ICT may contribute to reducing urban congestion and alleviating air quality problems. However, ICT may generate significant additional travel because of the increased connectivity and access to resources. Empirical insights on how the growing use of ICT affects travel
Experimental digital forensics of subscriber identification module (SIM) Card
[No abstract available]
Real-time vehicle detection and tracking using haar-like features and compressive tracking
This paper presents a real-time vision framework that detects and tracks vehicles from stationary camera. It can be used to calculate statistical information such as average traffic speed and flow as well as in surveillance tasks. The framework consists of three main stages. Vehicles are first detected using Haar-like features. In the second phase, an adaptive appearance-based model is built to dynamically keep track of the detected vehicles. This model is also used in the third phase of data association to fuse the detection and tracking results. The use of detection results to update the
Motion history of skeletal volumes and temporal change in bounding volume fusion for human action recognition
Human action recognition is an important area of research in computer vision. Its applications include surveillance systems, patient monitoring, human-computer interaction, just to name a few. Numerous techniques have been developed to solve this problem in 2D and 3D spaces. However 3D imaging gained a lot of interest nowadays. In this paper we propose a novel view-independent action recognition algorithm based on fusion between a global feature and a graph based feature. We used the motion history of skeleton volumes; we compute a skeleton for each volume and a motion history for each action
Arabic fake news detection using deep learning
Nowadays, an unprecedented number of users interact through social media platforms and generate a massive amount of content due to the explosion of online communication. However, because user-generated content is unregulated, it may contain offensive content such as fake news, insults, and harassment phrases. The identification of fake news and rumors and their dissemination on social media has become a critical requirement. They have adverse effects on users, businesses, enterprises, and even political regimes and governments. State of the art has tackled the English language for news and
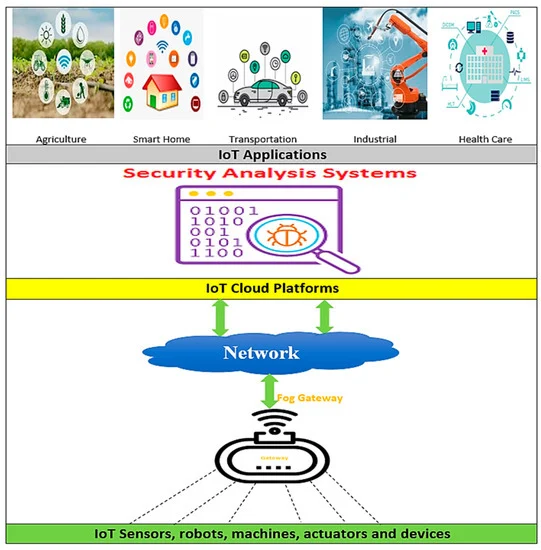
HSAS-MD Analyzer: A Hybrid Security Analysis System Using Model-Checking Technique and Deep Learning for Malware Detection in IoT Apps
Established Internet of Things (IoT) platforms suffer from their inability to determine whether an IoT app is secure or not. A security analysis system (SAS) is a protective shield against any attack that breaks down data privacy and security. Its main task focuses on detecting malware and verifying app behavior. There are many SASs implemented in various IoT applications. Most of them build on utilizing static or dynamic analysis separately. However, the hybrid analysis is the best for obtaining accurate results. The SAS provides an effective outcome according to many criteria related to the
Recognizing Clothing Patterns and Colors for BVI People Using Different Techniques
For blind and visually impaired (BVI) people, it is an arduous task to recognize clothing patterns and colors. It is especially complex to recognize them automatically. This is a highly researched area in image processing. This paper provides BVI with the ability to detect patterns and colors without depending on personal assistance, leading to increasing their confidence. The user first captures an image; then, our system detects colors and patterns. The color model used here is the hue saturation value (HSV). The main colors detected by our system are magenta, cyan, blue, green, red and
Transverse momentum spectra of strange hadrons within extensive and nonextensive statistics
Using generic (non)extensive statistics, in which the underlying system likely autonomously manifests its extensive and nonextensive statistical nature, we extract various fit parameters from the CMS experiment and compare these to the corresponding results obtained from Tsallis and Boltzmann statistics. The present study is designed to indicate the possible variations between the three types of statistical approaches and characterizes their dependence on collision energy, multiplicity, and size of the system of interest. We analyze the transverse momentum spectra pT of the strange hadrons Ks
AutoDLCon: An Approach for Controlling the Automated Tuning for Deep Learning Networks
Neural networks have become the main building block on revolutionizing the field of artificial intelligence aided applications. With the wide availability of data and the increasing capacity of computing resources, they triggered a new era of state-of-the-art results in diverse directions. However, building neural network models is domain-specific, and figuring out the best architecture and hyper-parameters in each problem is still an art. In practice, it is a highly iterative process that is very time-consuming, requires substantial computing resources, and needs deep knowledge and solid
Pagination
- Previous page ‹‹
- Page 4
- Next page ››
