TCAIOSC: Trans-Compiler Based Android to iOS Converter
Cross-platform development is the practice of developing software products or services for multiple platforms or software environments. The idea of cross-platform development is that a software application or product should work well in more than one specific digital habitat. This capability is typically pursued in order to sell software for more than one proprietary operating system. In general, cross-platform development can make a program less efficient. However, in many cases, the makers of software figured out that the limitations of cross-platform development are worth dealing with in
Change analysis for gait impairment quantification in smart environments
Visual Sensor Networks (VSNs) open up a new realm of smart autonomous applications based on enhanced three- dimensional sensing and collaborative reasoning. An emerging VSN application domain is pervasive healthcare delivery where gait information computed from distributed vision nodes is used for observing the wellbeing of the elderly, quantifying post-operative patient recovery and monitoring the progression of neurodegenerative diseases such as Parkinson's. The development of patient-specific gait analysis models, however, is challenging since it is unfeasible to obtain normal and impaired
Computer-aided analysis of fluorescein angiograms using colour leakage maps
Fundus fluorescein angiography (FFA) is a standard screening and diagnosis technique for several retinal diseases. The analysis of FFA images is performed qualitatively by skilled observers, and thus is vulnerable to inter- and intra-observer variability. In this study, the authors present a method for computer-aided analysis of FFA images. The method is based on generating quantitative colour fluorescein leakage maps (FLM) that mimic the thickness maps generated by the optical coherence tomography (OCT). Results from 64 patients show strong correlation between the FLM and OCT thickness maps
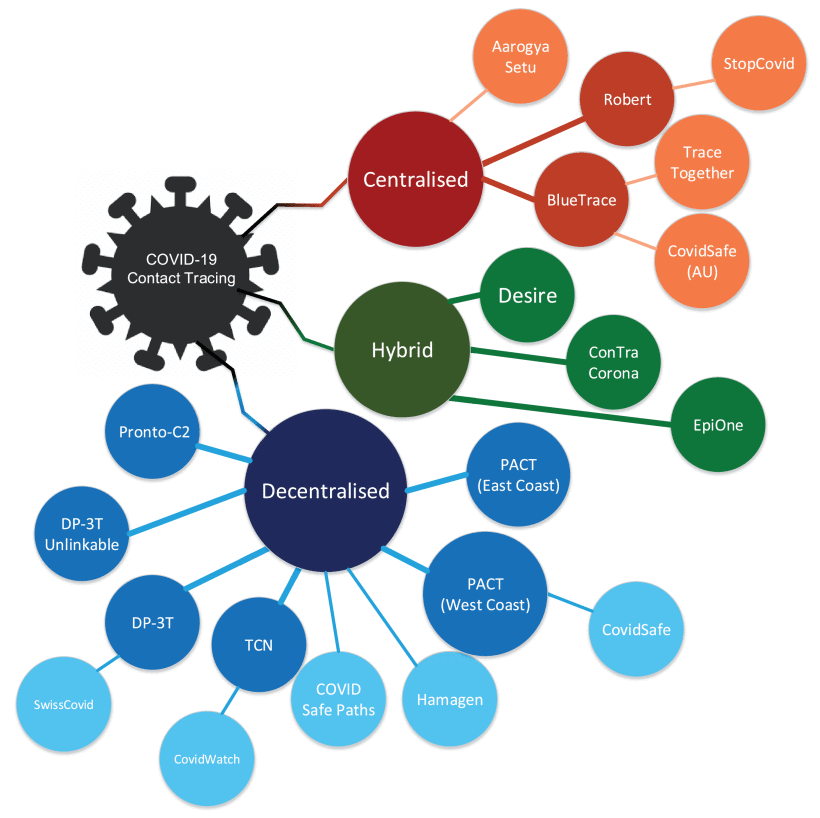
A Survey of COVID-19 Contact Tracing Apps
The recent outbreak of COVID-19 has taken the world by surprise, forcing lockdowns and straining public health care systems. COVID-19 is known to be a highly infectious virus, and infected individuals do not initially exhibit symptoms, while some remain asymptomatic. Thus, a non-negligible fraction of the population can, at any given time, be a hidden source of transmissions. In response, many governments have shown great interest in smartphone contact tracing apps that help automate the difficult task of tracing all recent contacts of newly identified infected individuals. However, tracing
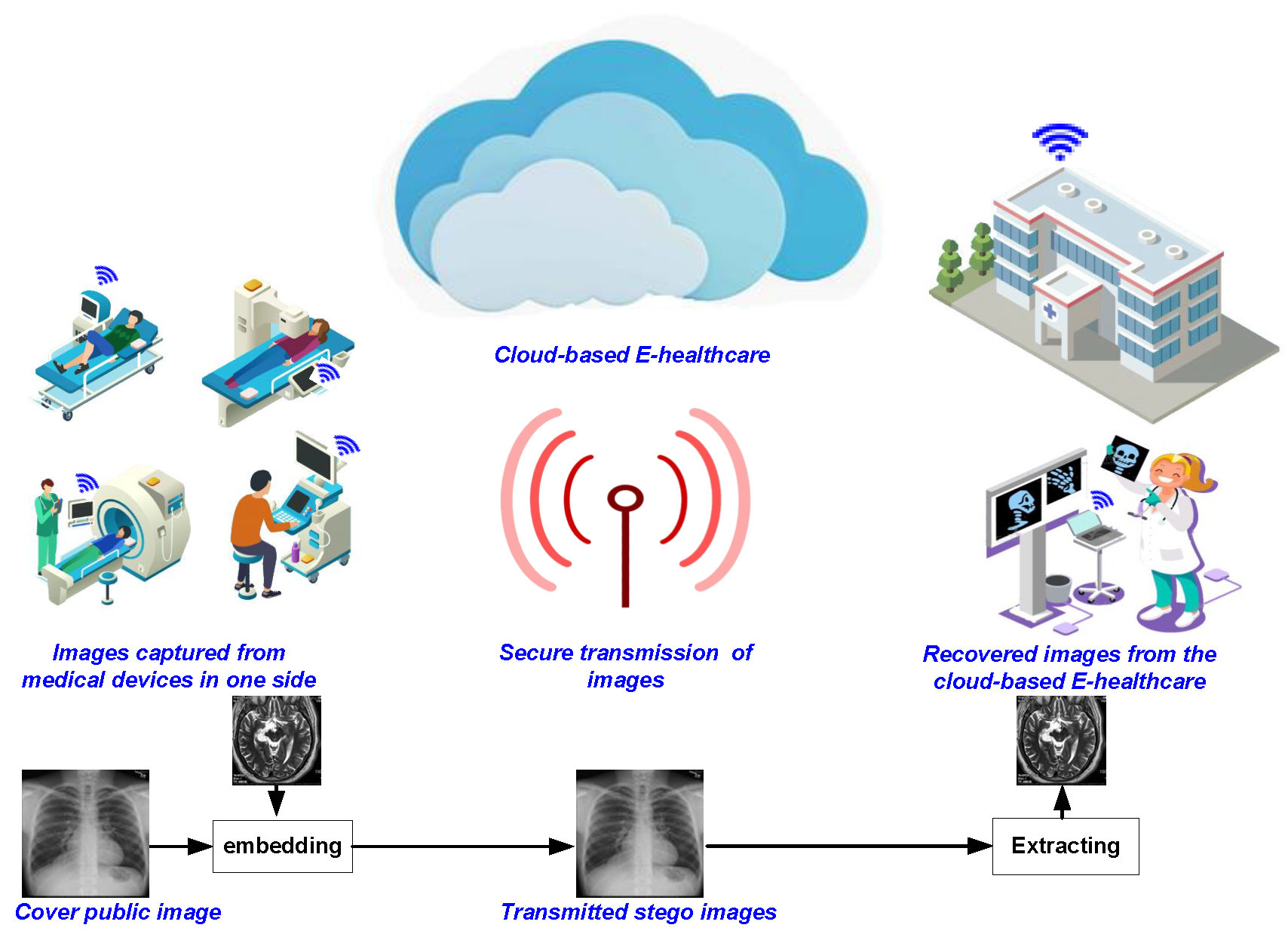
A robust quasi-quantum walks-based steganography protocol for secure transmission of images on cloud-based E-healthcare platforms
Traditionally, tamper-proof steganography involves using efficient protocols to encrypt the stego cover image and/or hidden message prior to embedding it into the carrier object. However, as the inevitable transition to the quantum computing paradigm beckons, its immense computing power will be exploited to violate even the best non-quantum, i.e., classical, stego protocol. On its part, quantum walks can be tailored to utilise their astounding ‘quantumness’ to propagate nonlinear chaotic behaviours as well as its sufficient sensitivity to alterations in primary key parameters both important
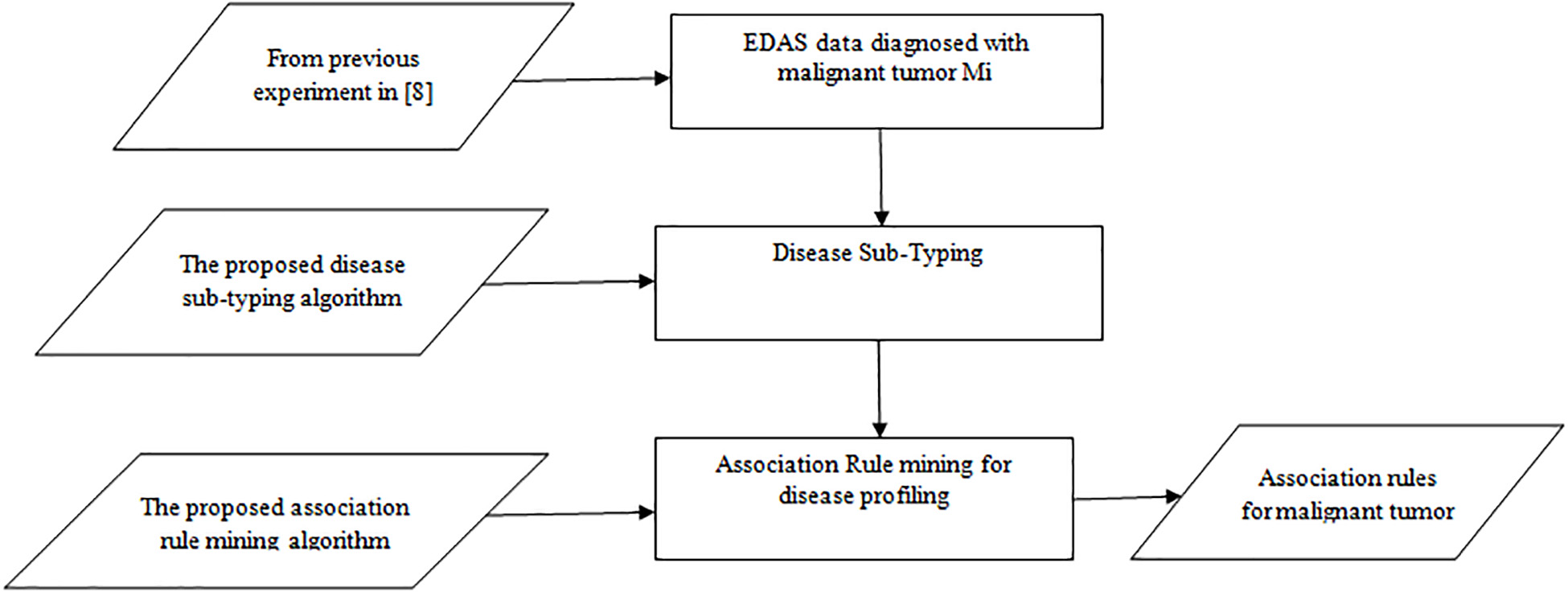
A Theoretical Approach for Correlating Proteins to Malignant Diseases
Malignant Tumors are developed over several years due to unknown biological factors. These biological factors induce changes in the body and consequently, they lead to Malignant Tumors. Some habits and behaviors initiate these biological factors. In effect, the immune system cannot recognize a Malignant Tumor as foreign tissue. In order to discover a fascinating pattern of these habits, behaviors, and diseases and to make effective decisions, different machine learning techniques should be used. This research attempts to find the association between normal proteins (environmental factors) and
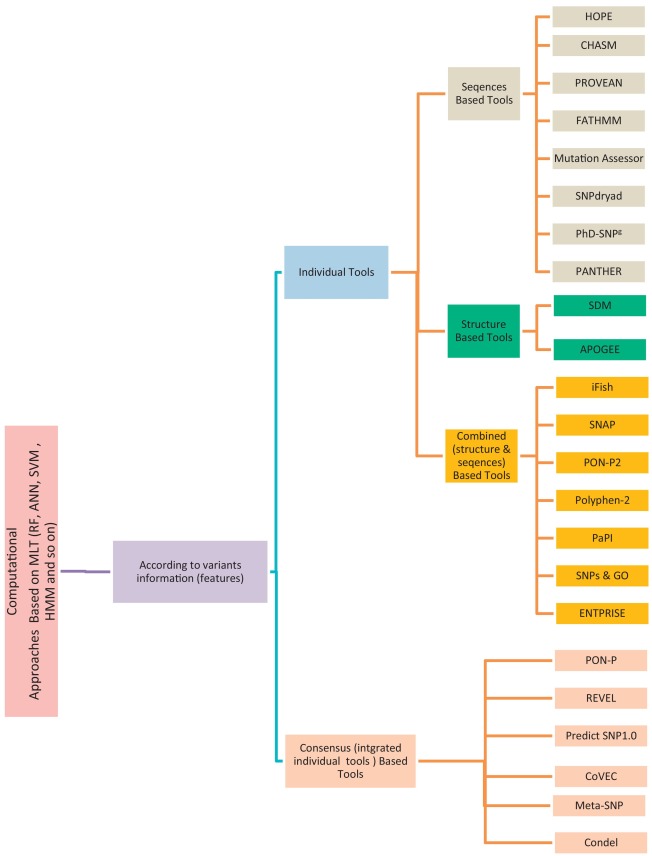
A review study: Computational techniques for expecting the impact of non-synonymous single nucleotide variants in human diseases
Non-Synonymous Single-Nucleotide Variants (nsSNVs) and mutations can create a diversity effect on proteins as changing genotype and phenotype, which interrupts its stability. The alterations in the protein stability may cause diseases like cancer. Discovering of nsSNVs and mutations can be a useful tool for diagnosing the disease at a beginning stage. Many studies introduced the various predicting singular and consensus tools that based on different Machine Learning Techniques (MLTs) using diverse datasets. Therefore, we introduce the current comprehensive review of the most popular and recent
Towards scalable and cost-aware bioinformatics workflow execution in the cloud - Recent advances to the tavaxy workflow system
Cloud-based scientific workflow systems can play an important role in the development of cost effective bioinformatics analysis applications. So far, most efforts for supporting cloud computing in such workflow systems have focused on simply porting them to the cloud environment. The next due steps are to optimize these systems to exploit the advantages of the cloud computing model, basically in terms of managing resource elasticity and the associated business model. In this paper, we introduce new advancements in designing scalable and cost-effective workflows in the cloud using the Tavaxy
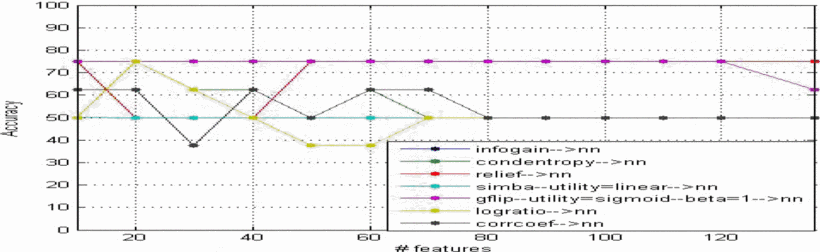
Feature selection in computer aided diagnostic system for microcalcification detection in digital mammograms
In this paper an approach is proposed to develop a computer-aided diagnosis (CAD) system that can be very helpful for radiologist in diagnosing microcalcifications' patterns in digitized mammograms earlier and faster than typical screening programs and showed the efficiency of feature selection on the CAD system. The proposed method has been implemented in four stages: (a) the region of interest (ROI) selection of 32x32 pixels size which identifies clusters of microcalcifications, (b) the feature extraction stage is based on the wavelet decomposition of locally processed image (region of
Extreme Points Derived Confidence Map as a Cue for Class-Agnostic Interactive Segmentation Using Deep Neural Network
To automate the process of segmenting an anatomy of interest, we can learn a model from previously annotated data. The learning-based approach uses annotations to train a model that tries to emulate the expert labeling on a new data set. While tremendous progress has been made using such approaches, labeling of medical images remains a time-consuming and expensive task. In this paper, we evaluate the utility of extreme points in learning to segment. Specifically, we propose a novel approach to compute a confidence map from extreme points that quantitatively encodes the priors derived from
Pagination
- Previous page ‹‹
- Page 14
- Next page ››
