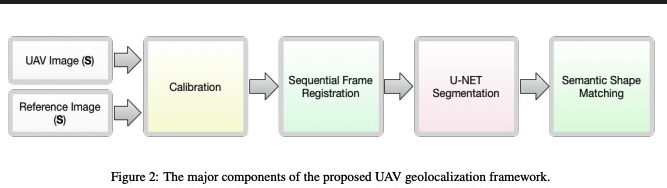
A deep CNN-based framework for enhanced aerial imagery registration with applications to UAV geolocalization
In this paper we present a novel framework for geolocalizing Unmanned Aerial Vehicles (UAVs) using only their onboard camera. The framework exploits the abundance of satellite imagery, along with established computer vision and deep learning methods, to locate the UAV in a satellite imagery map. It utilizes the contextual information extracted from the scene to attain increased geolocalization accuracy and enable navigation without the use of a Global Positioning System (GPS), which is advantageous in GPS-denied environments and provides additional enhancement to existing GPS-based systems
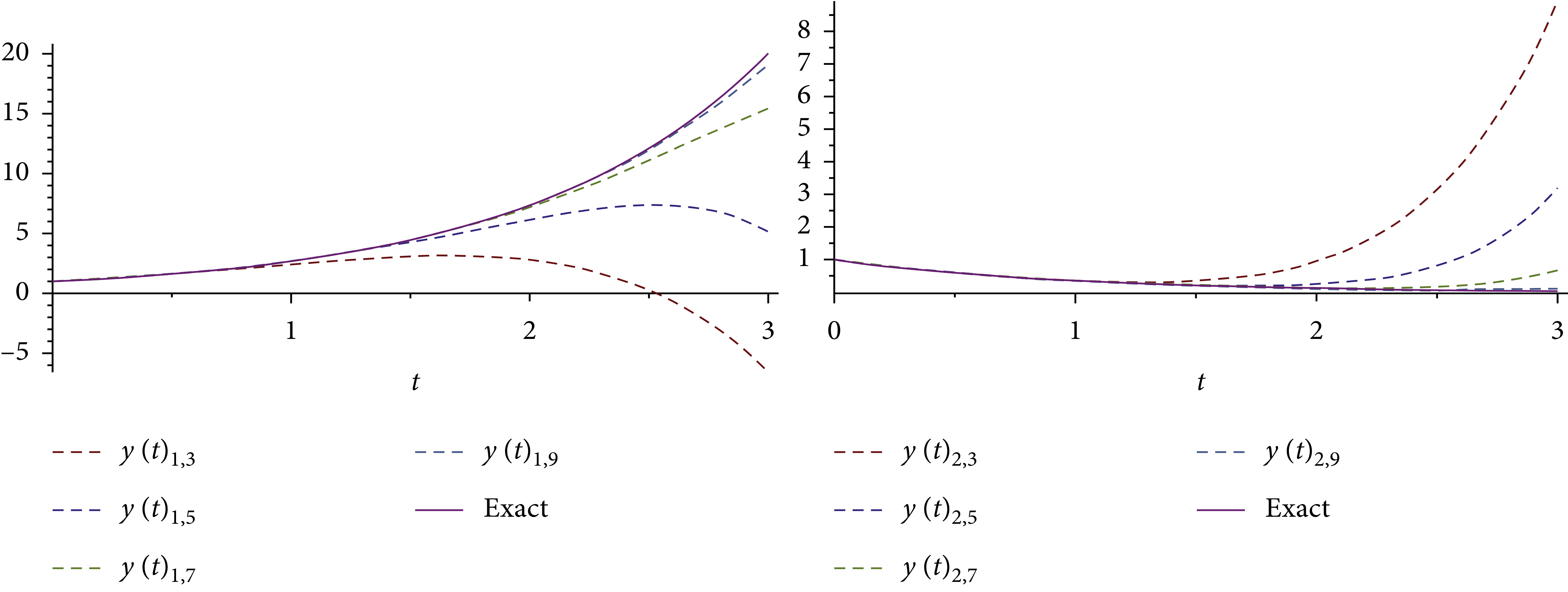
An Analytical Computational Algorithm for Solving a System of Multipantograph DDEs Using Laplace Variational Iteration Algorithm
In this research, an approximation symbolic algorithm is suggested to obtain an approximate solution of multipantograph system of type delay differential equations (DDEs) using a combination of Laplace transform and variational iteration algorithm (VIA). The corresponding convergence results are acquired, and an efficient algorithm for choosing a feasible Lagrange multiplier is designed in the solving process. The application of the Laplace variational iteration algorithm (LVIA) for the problems is clarified. With graphics and tables, LVIA approximates to a high degree of accuracy with a few
Multi projection fusion for real-time semantic segmentation of 3D LiDAR point clouds
Semantic segmentation of 3D point cloud data is essential for enhanced high-level perception in autonomous platforms. Furthermore, given the increasing deployment of LiDAR sensors onboard of cars and drones, a special emphasis is also placed on non-computationally intensive algorithms that operate on mobile GPUs. Previous efficient state-of-the-art methods relied on 2D spherical projection of point clouds as input for 2D fully convolutional neural networks to balance the accuracy-speed trade-off. This paper introduces a novel approach for 3D point cloud semantic segmentation that exploits

IoT Based AI and its Implementations in Industries
The Internet of Things (IoT) is an Internet revolution that is increasingly used in business, industry, medicine, the economy and other modern information society. IoT, particularly transport, industrial robots and automation systems are supported by artificial intelligence in a wide range of daily implementations with dominant industrial applications. IoT is an interconnected network of physical objects, which enables them to gather and share information, using software, sensor units and network connectivity. In industries; IoT brought about a new revolution in industries. In the field of IoT
Controlled alternate quantum walk-based pseudo-random number generator and its application to quantum color image encryption
Pseudo-random number generator (PRNG) are a key component in the design of modern cryptographic mechanisms and are regarded as a backbone element of many modern cryptographic applications. However and in spite of their robustness, quantum computers could crack down PNGR-based systems. Quantum walks, a universal model of quantum computation, have nonlinear properties that make them a robust candidate to produce PRNG. In this paper, we utilize controlled alternate quantum walk (CAQW) to create PRNG. Moreover, we use the presented PRNG mechanism as a component of a new quantum color image
Combating sybil attacks in vehicular ad hoc networks
Vehicular Ad Hoc Networks (VANETs) are considered as a promising approach for facilitating road safety, traffic management, and infotainment dissemination for drivers and passengers. However, they are subject to an attack that has a severe impact on their security. This attack is called the Sybil attack, and it is considered as one of the most serious attacks to VANETs, and a threat to lives of drivers and passengers. In this paper, we propose a detection scheme for the Sybil attack. The idea is based on public key cryptography and aims to ensure privacy preservation, confidentiality, and non
Complexwavelet Transform Cwt Based Video Magnification for 3d Facial Video Identification
Magnifying micro changes in motion and brightness of videos that are unnoticeable by the human visual system have recently been an interesting area to explore. In this paper, we explore this technique in 3D facial video identification, we utilize this technique to identify 3D objects from 2D images. We present a Complex Wavelet Transform CWT, 2D-Dual CWT based technique, to calculate any changes between subsequent video frames of CWT sub-bands at different spatial locations. In this technique, a gradient based method is proposed to determine the orientation of each CWT sub band in addition to
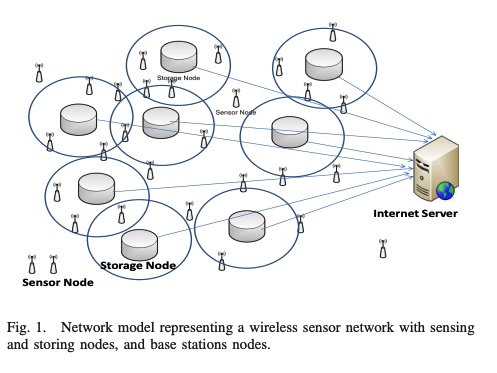
A distributed data collection algorithm for wireless sensor networks with persistent storage nodes
A distributed data collection algorithm to accurately store and forward information obtained by wireless sensor networks is proposed. The proposed algorithm does not depend on the sensor network topology, routing tables, or geographic locations of sensor nodes, but rather makes use of uniformly distributed storage nodes. Analytical and simulation results for this algorithm show that, with high probability, the data disseminated by the sensor nodes can be precisely collected by querying any small set of storage nodes.
Real-time scale-adaptive compressive tracking using two classification stages
In this paper, we describe a method for Scale-Adaptive visual tracking using compressive sensing. Instead of using scale-invariant-features to estimate the object size every few frames, we use the compressed features at different scale then perform a second stage of classification to detect the best-fit scale. We describe the proposed mechanism of how we implement the Bayesian Classifier used in the algorithm and how to tune the classifier to address the scaling problem and the method of selecting the positive training samples and negative training samples of different scales. The obtained
Tavaxy: Integrating Taverna and Galaxy workflows with cloud computing support
Background: Over the past decade the workflow system paradigm has evolved as an efficient and user-friendly approach for developing complex bioinformatics applications. Two popular workflow systems that have gained acceptance by the bioinformatics community are Taverna and Galaxy. Each system has a large user-base and supports an ever-growing repository of application workflows. However, workflows developed for one system cannot be imported and executed easily on the other. The lack of interoperability is due to differences in the models of computation, workflow languages, and architectures of
Pagination
- Previous page ‹‹
- Page 13
- Next page ››
